How can we manage to secure global supply chains?
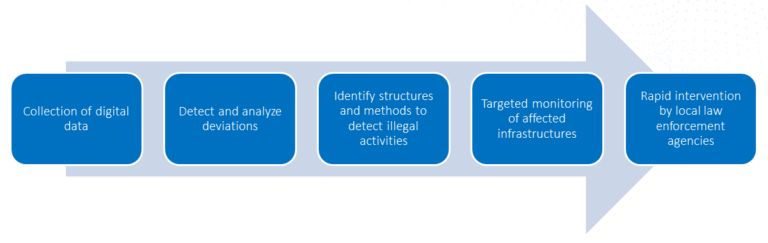
The business processes and financial transactions are digitally mapped and thus leave evaluable digital traces. Today, it is almost impossible to do business without leaving digital traces – even if supply chains run across the sea.
Behind every illegal activity are data streams (e.g.: business and organizational data) that can be identified and analyzed. Deviations from the legal process chains indicate criminal activities.
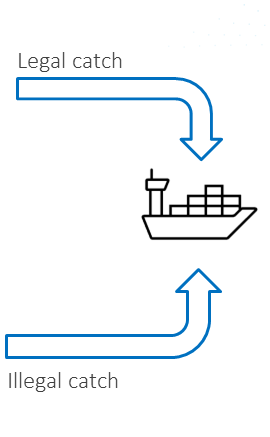
Within NEMO the entire legal supply chain will be analysed, to detect anomalies and at what point the legal supply chain is being abused for illegal activity. Anomalies can only be detected if the legal process and supply chain is known!
For the development of a generic crime model, two scenarios are fully explored:
SCENARIO 1: ILLEGAL FISHING
Using the example of bluefin tuna
SCENARIO 2: ILLEGAL TROPICAL TIMBER TRADE
Using the example of a species of tropical wood from Indonesia
Deutor will provide the majority of work packages 2 and 3 (analysis of the process and supply chains and creation of the crime model) and use this knowledge regarding the use of data sources to identify illegal maritime activities, with the help of Fraunhofer IOSB, Airbus and Arina.
